Get the Reddit app
A subreddit for private and government security professionals around the globe.

patrol or static? what do you prefer?
Getting offered a schedule of overnight patrolling instead of a more static with some minor patrolling (patrol between multiple stores with static). I like that I will only work 3 days a week but it's 12h shifts.
I like static because I feel like I'm making a bigger difference as I'm protecting stores that are actively being used. Idk how I would feel About patrolling around when most people are asleep and stores are closed. I guess it may be the same thing if I get into law enforcement and have to patrol on night shift.
But idk how I feel about it.
Which do you prefer? What's your opinion?
By continuing, you agree to our User Agreement and acknowledge that you understand the Privacy Policy .
Enter the 6-digit code from your authenticator app
You’ve set up two-factor authentication for this account.
Enter a 6-digit backup code
Create your username and password.
Reddit is anonymous, so your username is what you’ll go by here. Choose wisely—because once you get a name, you can’t change it.
Reset your password
Enter your email address or username and we’ll send you a link to reset your password
Check your inbox
An email with a link to reset your password was sent to the email address associated with your account
Choose a Reddit account to continue

- Services Mobile Patrols Electronic Security Security Personnel Emergency & Medical Corporate Risk & Resilience Major Events
- Sectors Aviation Commercial Real Estate Defence Security Education Finance & Banking Government Healthcare Resources Retail Transport Utilities & Telecom
- Solutions Access Control CCTV & Analytics Alarm Systems & Remote Monitoring Mobile & Autonomous Security Canine Security
- Insights Innovating Security for Tomorrow Blog News Whitepapers Case Studies Brochures & Flyers
- Sustainability 2023/24 Sustainability Report Corporate Social Responsibility Indigenous Engagement Health and Safety
- About Our Integrated Approach Our Values Our History Our Leadership Team Our Locations National Operations Centre Our Policies Contact Us
- Careers Why Us STRIVE Awards Current Vacancies
- 1300 945 766
Do I need static security personnel or mobile patrols?

Every business owner wants to know that their assets are secure, but how best to do it? With each property requiring a unique response and with a range of security options to choose from, building and implementing a security framework that protects your business can be difficult.
Fortunately, the process can be simplified. Determining the kind of security staffing arrangement your property requires is key, and this can help shape the rest of your framework. Central to the question of security staffing is, do you need static security personnel or mobile patrols? While both add a human element to your security framework, they are suited to different areas and have unique operational requirements that must be considered.
To help you make a more informed choice, Wilson Security has put together a few points to consider when making security staffing decisions for your business. Read on and ensure your organisation has the protection it needs.
Suiting different kinds of sites
Key to making the right decision is understanding the specific needs of your property, and how different security solutions may serve these needs. It is self-evident that the security needs of a jewellery store are going to differ significantly from those of a construction site, but have you considered the different needs of different jewellery stores? Your location, your assets, your business activities – all of these will impact the nature of the threats you face and the types of security responses that are required to counter them. In light of this, it's important to keep the relative strengths of static security and mobile patrols in mind.
Static security personnel are best suited in locations where constant surveillance of people or assets operating in a fixed area are required. Whether this is high-value stock in a retail space or secure areas in a building, static securitiy personnel are able to provide the unbroken surveillance you need to minimise the chance of a breach.
Conversely, mobile patrols are more suited to areas where assets are either physically larger or distributed over a wider area, such as industrial facilities or construction sites. This is not to say to the assets under their protection have a lower monetary value than those protected by static security personnel, rather that because of their size or design they are harder to remove from the location. Consider the difference between cash or jewellery and construction equipment or commercial vehicles. Often these assets will be stored on larger properties, making constant surveillance of all items prohibitively expensive or simply not feasible.

The possibility for providing additional services
When considering your choice of security staffing solution, it is important to think about how this fits into their overall operations. Savvier owners may be able to further enhance productivity or customer satisfaction with the right security team.
Beyond confirming asset security, mobile patrols can also be used to provide maintenance checks and hazard reporting, filing reports throughout their shift in addition to their normal duties. This not only keeps your assets safe from vandalism or theft, but contributes to keeping your employees safe from faulty equipment and on-the-job accidents.
The right static security personnel can offer you a new way to engage with customers. Whether you're welcoming clients into an office or buyers into a store, concierge security personnel can provide both the information customers need to make decisions as well as the protection your organisation requires. Training will differ depending on requirements, but concierge security have served as receptionists, tour guides, retail assistants and more, fitting into a wide variety of roles and corporate structures.
A difference in perception
Businesses should consider how the choice of security personnel affects the public perception of the company. Uniformed static security personnel have the potential to be perceived as imposing. Depending on your business, this may work for or against you, either intimidating customers away from a sale or sending a clear message to business partners that you take their security and the security of your organisation seriously. Equally, mobile patrols can project an air of efficiency and agility, demonstrating an ability to respond to changing circumstances in a measured and precise way. Carefully consider how your chosen security staffing solution presents your business.
View our blog terms and conditions here .
Contact us to find out how Wilson Security can secure your business
Related Articles
8 things to consider when engaging a mobile security service, the role of private security in creating safe cities, empowering communities with the reconciliation action plan.

Wilson Security acknowledges the Traditional Custodians of the land on which we work and live and recognise their continuing connection to land, sea and culture. We pay respect to Elders past, present, emerging and extend that respect to all Aboriginal and Torres Strait Islander people around the country.

- Private Security
- Top-Rated 24 Hour Security Guard
- Unarmed Security service
- Fire watch security service
- Construction security services
- Event security service
- Mobile Security Patrol Services
- Executive Protection Services
- Orange County
- Riverside County
- San Bernardino County
- San Fernando Valley
- Santa Barbara
- San Diego County
- San Gabriel Valley
- Ventura County
- Security Guards for Commercial Properties
- College Universities
- Security for Commercial-Properties
- High Rise Building
- Medical Facilities
- Parking Lots and Structure
- Places Of Worships
- Security for Retail Centers
- Security for Industrial Complexes
Guidelines for Security Guard Patrols That Work
October 30, 2023

In today’s world, maintaining a safe and secure environment is of paramount importance. Security guard patrols, an essential aspect of security guard services , play a crucial role in ensuring the safety and protection of people and properties By implementing effective patrol procedures, security guards can effectively deter, detect, and respond to potential threats. In this article, we will explore the key components of security guard patrol procedures and provide practical guidance on how to execute them efficiently.
Security guard patrols are an integral part of maintaining safety and security Guard Patrols. They serve as a proactive measure to prevent crime, detect suspicious activities, and respond to emergencies promptly. Patrolling not only helps to establish a visible deterrent but also provides an opportunity to gather valuable intelligence. By adhering to well-defined patrol procedures, security guards can enhance the overall effectiveness of their operations.
Pre-Patrol Procedures
Before starting a patrol, security guards must ensure they are adequately prepared. This involves several essential pre-patrol procedures:
- Checking in and receiving assignments : Security guards should report to their supervisors or designated personnel to receive their patrol assignments. This ensures proper communication and alignment of responsibilities.
- Gathering necessary equipment : Depending on the nature of the patrol, security guards may need to gather specific equipment such as flashlights, radios, keys, or personal protective gear. It is essential to have all the required tools readily available before commencing the patrol. This step is crucial in security patrol services , ensuring that every detail is accounted for optimal performance.
- Reviewing patrol routes : Familiarity with the patrol routes is crucial for efficient and effective patrols. Security guards should review the designated routes, paying attention to key areas, potential vulnerabilities, and any recent incidents or changes in the environment. This knowledge will enable them to make informed decisions during the patrol.
Starting the Patrol
Once all pre-patrol procedures are completed, the patrol can be commenced by security guards. The initial steps are crucial in setting the tone for a successful and vigilant patrol:
- Logging the start time : It is essential to record the exact start time of the patrol. This helps in maintaining accurate records and provides a reference point for any incidents or observations made during the patrol.
- Assessing the area : Before commencing the patrol, security guards should conduct a thorough assessment of the area. This includes checking for any signs of forced entry, damage, or suspicious activities. By establishing a baseline understanding of the environment, security guards can quickly identify any deviations during the patrol.
Patrol Techniques
During the patrol, security guards must employ various techniques to ensure maximum effectiveness. These techniques include:
- Vigilant monitoring of entrances and exits : Security guards should pay close attention to all entrances and exits, ensuring they are secure and free from any unauthorized access. This includes checking for broken locks, propped-open doors, or any signs of tampering.
- Identifying out-of-place objects or signs : Security guards should be observant and vigilant in identifying any objects or signs that appear out of place. This could be a broken window, misplaced items, or unfamiliar markings. These anomalies may indicate potential security threats or breaches.
- Observing behavioral changes : The behavior of individuals within the patrol area should be observed and assessed by security guards, who should be trained for this purpose. Note and report any sudden changes in behavior, such as nervousness, aggression, or suspicious activities, accordingly.
- Scanning for suspicious elements : Security guards should maintain a high level of awareness and actively scan the surroundings for any suspicious elements. This includes keeping an eye out for unattended bags, suspicious individuals, or any unusual activities that may pose a threat to the safety and security of the area.
By incorporating these patrol techniques into their routine, security guards can significantly enhance their ability to detect and respond to potential security risks.
Interacting with the Public
Security guards often interact with the public during their patrols. It is essential to approach these interactions professionally while remaining vigilant for any signs of suspicious activities. Key considerations for interacting with the public include:
- Handling inquiries professionally : Security guards should be prepared to handle inquiries from the public, including providing directions, answering questions, or assisting with general inquiries. It is crucial to maintain a helpful and professional demeanor while remaining alert to any potential security concerns.
- Identifying suspicious activities : While engaging with the public, security guards should be trained to identify any suspicious activities or behaviors. This could include individuals loitering for extended periods, attempting unauthorized access, or engaging in aggressive or erratic behavior. Prompt reporting of such activities is essential for maintaining security.
Maintaining a balance between professionalism and vigilance by security guards can effectively ensure the safety and security of both the public and the premises entrusted to protection.
Emergency Procedures
In emergency situations, security guards play a critical role in ensuring a swift and effective response. Well-versedness in emergency procedures, including the following, is essential for security guards.
- Fire emergencies : In the event of a fire, security guards should be trained to respond quickly, following established evacuation protocols, and assisting occupants in a calm and orderly manner. This may involve sounding alarms, guiding individuals to designated assembly points, or providing assistance to those in need.
- Medical emergencies : Security guards should be trained in basic first aid and CPR to provide immediate assistance in medical emergencies. They should be able to assess the situation, administer first aid if necessary, and promptly alert emergency medical services for further assistance.
- Security breaches : In the event of a security breach, security guards should be prepared to implement appropriate response protocols. This may include securing the area, alerting relevant authorities, and providing accurate and timely information to support a comprehensive response.
By having well-defined emergency procedures in place and conducting regular training exercises, security guards can effectively respond to emergencies, minimizing potential risks and ensuring the safety of all individuals involved.
End of Patrol Procedures
At the conclusion of a patrol, security guards must follow specific procedures to ensure a seamless transition and maintain the security of the area:
- Completing patrol logs : Security guards should diligently record all observations, incidents, and actions taken during the patrol in a detailed patrol log. This documentation serves as a crucial record for future reference and aids in maintaining accurate incident reports.
- Securing the area : Before leaving the patrol area, security guards should ensure that all doors, windows, and access points are properly secured. This includes checking for any signs of tampering or unauthorized entry and reporting any irregularities to the appropriate authorities.
By adhering to these end-of-patrol procedures, security guards can ensure the continuity of security measures and provide a smooth transition for the next patrol shift.
Post-Patrol Responsibilities
Beyond the completion of a patrol, security guards have additional post-patrol responsibilities that contribute to the overall effectiveness of security operations:
- Debriefing : Security guards may be required to participate in debriefing sessions with supervisors or team members. These sessions provide an opportunity to share observations, discuss any incidents or concerns, and exchange relevant information for ongoing security efforts.
Detailed and comprehensive reporting enables the enabling of proactive measures to effectively address security risks.
By actively engaging in post-patrol responsibilities, security guards contribute to the continuous improvement and refinement of security operations.
Real-Life Examples
To illustrate the practical application of patrol procedures, let’s consider two real-life examples:
- Corporate Office : In a corporate office setting, security guards may conduct regular patrols to ensure the safety and security of the premises. They would diligently monitor entrances and exits, conduct thorough inspections of key areas, and interact professionally with employees and visitors. During emergencies, they would follow established protocols, assist in evacuations, and provide support to emergency responders.
- Retail Store : In a retail store, security guards play a crucial role in deterring theft and ensuring customer safety. They would actively patrol the store, paying close attention to high-risk areas such as entrances, exits, and aisles. They would also monitor surveillance cameras, respond to suspicious activities, and provide assistance to customers when needed.
These examples highlight the practical implementation of security guard patrol procedures in different settings, emphasizing the importance of vigilance and adherence to established protocols.
Effective security guard patrol procedures are essential for maintaining safety and security in a wide range of settings. By following pre-patrol procedures, employing vigilant patrol techniques, and responding effectively to emergencies, security guards can fulfill their role in deterring threats, detecting suspicious activities, and ensuring the overall safety of people and assets.
While it is crucial for Security Guard Patrols to approach their duties with professionalism, attentiveness, and a commitment to ongoing training and improvement. By adhering to best practices and continuously refining their skills. Security guards can make a significant impact in creating a safe and secure environment for all.
Remember, security guard patrol procedures are not only about physical presence but also about the ability to adapt to changing circumstances, communicate effectively, and make informed decisions. By integrating these principles into their patrol procedures. Security guards can fulfill their crucial role in maintaining safety and security in today’s complex and ever-evolving world.
Related Posts

Construction Site Security Guards in Los Angeles
Construction Site Security in Los Angeles are bustling hubs of activity, where progress and development shape the city’s skyline. However,

The Advantages of Mobile Patrol Security Services in 2024
We cannot deny the fact that we need security services to safeguard our property and loved ones. Traditional security measures,

Why You Need Professional Apartment Security Services in 2024
In 2024, apartment living is more than just a space—it’s a dynamic hub where personal and professional lives intersect. Imagine
- Los Angeles County
- Santa Barbara County
- Event Security
- Fire Watch Security
- Mobile Patrol Security
- Unarmed Security Guard
- Social Media Links GET IN TOUCH
Stay in touch with us. You can find us on the following social media platforms.
Static Routing Configuration Guide with Examples
This tutorial explains how to configure static routing on routers. Learn how to create and manage static routes on routers through a packet tracer example.
Static routes are the routes you manually add to the router’s routing table. The process of adding static routes to the routing table is known as static routing. Let’s take a packet tracer example to understand how to use static routing to create and add a static route to the routing table.
Setting up a practice lab
Create a packet tracer lab as shown in the following image or download the following pre-created lab and load it on Packet Tracer.
Packet Tracer Lab with Initial IP Configuration

In this lab, each network has two routes to reach. We will configure one route as the main route and another route as the backup route. If the link bandwidth of all routes is the same, we use the route that has the least number of routers as the main route. If the link bandwidth and the number of routers are the same, we can use any route as the main route and another route as the backup route.
If we specify two routes for the same destination, the router automatically selects the best route for the destination and adds the route to the routing table. If you manually want to select a route that the router should add to the routing table, you have to set the AD value of the route lower than other routes. For example, if you use the following commands to create two static routes for network 30.0.0/8, the route will place the first route to the routing table.
If the first route fails, the router automatically adds the second route to the routing table.
Creating, adding, verifying static routes
Routers automatically learn their connected networks. We only need to add routes for the networks that are not available on the router’s interfaces. For example, network 10.0.0.0/8, 20.0.0.0/8 and 40.0.0.0/8 are directly connected to Router0. Thus, we don’t need to configure routes for these networks. Network 30.0.0.0/8 and network 50.0.0.0/8 are not available on Router0. We have to create and add routes only for these networks.
The following table lists the connected networks of each router.
| Router | Available networks on local interfaces | Networks available on other routers’ interfaces |
| Router0 | 10.0.0.0/8, 20.0.0.0/8, 40.0.0.0/8 | 30.0.0.0/8, 50.0.0.0/8 |
| Router1 | 20.0.0.0/8, 30.0.0.0/8, 50.0.0.0/8 | 10.0.0.0/8, 40.0.0.0/8 |
| Router2 | 40.0.0.0/8, 50.0.0.0/8 | 10.0.0.0/8, 20.0.0.0/8, 30.0.0.0/8 |
Let's create static routes on each router for networks that are not available on the router.
Router0 requirements
- Create two routes for network 30.0.0.0/8 and configure the first route (via -Router1) as the main route and the second route (via-Router2) as a backup route.
- Create two routes for the host 30.0.0.100/8 and configure the first route (via -Router2) as the main route and the second route (via-Router1) as a backup route.
- Create two routes for network 50.0.0.0/8 and configure the first route (via -Router2) as the main route and the second route (via-Router1) as a backup route.
- Verify the router adds only main routes to the routing table.
Router0 configuration
Access the CLI prompt of Router0 and run the following commands.

Router1 requirements
- Create two routes for network 10.0.0.0/8 and configure the first route (via -Router0) as the main route and the second route (via-Router1) as a backup route.
- Create two routes for network 40.0.0.0/8 and configure the first route (via -Router0) as the main route and the second route (via-Router2) as a backup route.
Router1 configuration

Router2 requirements
Create static routes for network 10.0.0.0/8 and network 30.0.0.0/8 and verify the router adds both routes to the routing table.
Router2 configuration

Verifying static routing
On Router0, we configured two routes for network 30.0.0.0/8. These routes are via Router1 and via Router2. We set the first route (via-Router1) as the main route and the second route as the backup route. We can verify this configuration in two ways.
By sending ping requests to a PC of network 30.0.0.0/8 and tracing the path they take to reach the network 30.0.0.0/8. For this, you can use 'tracert' command on a PC of network 10.0.0.0/8. The 'tracert' command sends ping requests to the destination host and tracks the path they take to reach the destination.
By listing the routing table entries on Router0. Since a router uses the routing table to forward data packets, you can check the routing table to figure out the route the router uses to forward data packets for each destination.
The following image shows the above testing.

We also configured a separate static host route for the host 30.0.0.100/8. The router must use this route to forward data packets to the host 30.0.0.100/8. To verify this, you can do the same testing for the host 30.0.0.100/8.
The following image shows this testing.

We also configured a backup route for network 30.0.0.0/8. The router must put the backup route to the routing table and use it to forward data packets to network 30.0.0.0/8 when the main route fails. To verify this, we have to simulate the failure of the main route.
To simulate the failure of the main route, you can delete the link between Router0 and Router1. After deleting the link, do the same testing again for the network 30.0.0.0/8.

The following link provides the configured packet tracer lab of the above example.
Packet Tracer Lab with Static Routing Configuration
Deleting a static route
To delete a static route, use the following steps.
- Use the 'show ip route static' command to print all static routes.
- Note down the route you want to delete.
- Use the 'no ip route' command to delete the route.
If you have a backup route, the backup route becomes the main route when you delete the main route.
In our example, we have a backup route and a main route for the host 30.0.0.100/8. The following image shows how to delete both routes.

That’s all for this tutorial. In this tutorial, we discussed static routing and learned how to create, add, and manage static routes on the router.
By ComputerNetworkingNotes Updated on 2018-01-22
ComputerNetworkingNotes CCNA Study Guide Static Routing Configuration Guide with Examples
- EtherChannel Load Distribution Explained
- Link Aggregation Control Protocol (LACP) Explained
- Port Aggregation Protocol (PAgP) Explained
- EtherChannel Manual Configuration
- EtherChannel Basic Concepts Explained
- STP, RSTP, PVST, RPVST, and MSTP
- Similarities and Differences between STP and RSTP
- RSTP / RPVST Explained with Examples
- PVST/RPVST and EtherChannel Explained
- STP/RSTP Timers Explained
We do not accept any kind of Guest Post. Except Guest post submission, for any other query (such as adverting opportunity, product advertisement, feedback, suggestion, error reporting and technical issue) or simply just say to hello mail us [email protected]

Signal 8 Security
65 Our Lady
Triq San Tumas Fenech
Static Manned Guards Vs Mobile Patrolling: Which One Should I Choose?
Posted on: 24/01/2019.
When it comes to protecting your property or business, having on-site security acts as an excellent deterrent to potential crime. So what exactly is the difference between static manned guarding and mobile security patrols and how does one go about choosing? Leading security services in Malta – Signal 8 Security – looks into what defines both of them.
Static manned guards
Multiple studies have shown the effectiveness of physical security in preventing crimes. The psychological impact of human presence has been well-documented as a deterrent towards would-be burglars and criminals. Static manned guarding is generally the preferred security choice for those looking for someone to guard the entrance to a retail outlet or an event, as they are responsible for preventing unauthorised access and reducing the likelihood of disorderly behaviour. Other than acting as a great deterrent, static manned guards create a secure presence, giving event goers and shoppers peace of mind.
Mobile Security Patrol
Mobile security patrols are simply security guards that move around your premises to ensure order. This might be particularly relevant out of hours, when crime might be more likely. While a CCTV system with the latest sensors and alarms is helpful to monitor a wide area, there will be places that the cameras can’t reach. Plus, in case of illegal behaviour, human intervention is required to catch any offenders quickly. Therefore, it is necessary to have trained eyes at your premises, patrolling and monitoring your CCTV to ensure all security needs are being taken care of.
Retail shopping centres, car parks and residential communities have unique security needs. While some locations need a 24-hour security presence, others require an officer to patrol different places at random times. In short, choosing between having static manned guarding or mobile security and the frequency of which your site would be patrolled really depends on your business, the size of the premises and what you’re aiming to achieve by investing in on-site security guards.
Why choose Signal 8 when looking for security services in Malta ?
With years of experience in the field, you can rest assured that you and your premises will be in good hands with Signal 8 Security. As top providers of security services in Malta , we invest in our staff and their proper training so as to ensure quality and that your needs are met. Contact us now for more information about the bespoke services we provide.
Follow us on Facebook for regular updates!

Navigation Menu
Search code, repositories, users, issues, pull requests..., provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications You must be signed in to change notification settings
SSA Tutorial
haotianmichael/ssa-compiler-book
Folders and files.
| Name | Name | |||
|---|---|---|---|---|
| 6 Commits | ||||
| ocaml | ocaml | |||
Repository files navigation
Ssa-compiler-book, 0. introduction.
Static single assignment, known as SSA , was once developed at IBM Research. Because of its fast and powerful abilities on optimizations, most of the current commercial and open-source compilers, including LLVM , GCC , HotSpot , V8 engine , use SSA as a key IR for program analysis and other usages. On the other hand, research about Intermediate Representation such as MLIR became more mature.
This book aims to introduce SSA and explore related techniques in compiler field such program analysis and MLIR.
1. Prerequisites
As prerequisites, you need to know:
- functional languages , (Ocaml is good)
- static program analysis , (Dataflow and fixed point)
- compilers ,(Implementations and usages of IR and CodeGen )

2. TextBook
We use the well-known ssa-book as textbook to learn SSA . Here is my learning notes in Chinese.
3. Advanced
TODO: LLVM IR, MLIR, Relay...
3.2. Projects
TODO: Ocaml, Cpp...
- OCaml 100.0%
Lesson 5: Global Analysis & SSA
- global analysis & optimization
- static single assignment
- SSA slides from Todd Mowry at CMU another presentation of the pseudocode for various algorithms herein
- Revisiting Out-of-SSA Translation for Correctness, Code Quality, and Efficiency by Boissinot on more sophisticated was to translate out of SSA form
- tasks due October 7
Lots of definitions!
- Reminders: Successors & predecessors. Paths in CFGs.
- A dominates B iff all paths from the entry to B include A .
- The dominator tree is a convenient data structure for storing the dominance relationships in an entire function. The recursive children of a given node in a tree are the nodes that that node dominates.
- A strictly dominates B iff A dominates B and A ≠ B . (Dominance is reflexive, so "strict" dominance just takes that part away.)
- A immediately dominates B iff A dominates B but A does not strictly dominate any other node that strictly dominates B . (In which case A is B 's direct parent in the dominator tree.)
- A dominance frontier is the set of nodes that are just "one edge away" from being dominated by a given node. Put differently, A 's dominance frontier contains B iff A does not strictly dominate B , but A does dominate some predecessor of B .
- Post-dominance is the reverse of dominance. A post-dominates B iff all paths from B to the exit include A . (You can extend the strict version, the immediate version, trees, etc. to post-dominance.)
An algorithm for finding dominators:
The dom relation will, in the end, map each block to its set of dominators. We initialize it as the "complete" relation, i.e., mapping every block to the set of all blocks. The loop pares down the sets by iterating to convergence.
The running time is O(n²) in the worst case. But there's a trick: if you iterate over the CFG in reverse post-order , and the CFG is well behaved (reducible), it runs in linear time—the outer loop runs a constant number of times.
Natural Loops
Some things about loops:
- Natural loops are strongly connected components in the CFG with a single entry.
- Natural loops are formed around backedges , which are edges from A to B where B dominates A .
- A natural loop is the smallest set of vertices L including A and B such that, for every v in L , either all the predecessors of v are in L or v = B .
- A language that only has for , while , if , break , continue , etc. can only generate reducible CFGs. You need goto or something to generate irreducible CFGs.
Loop-Invariant Code Motion (LICM)
And finally, loop-invariant code motion (LICM) is an optimization that works on natural loops. It moves code from inside a loop to before the loop, if the computation always does the same thing on every iteration of the loop.
A loop's preheader is its header's unique predecessor. LICM moves code to the preheader. But while natural loops need to have a unique header, the header does not necessarily have a unique predecessor. So it's often convenient to invent an empty preheader block that jumps directly to the header, and then move all the in-edges to the header to point there instead.
LICM needs two ingredients: identifying loop-invariant instructions in the loop body, and deciding when it's safe to move one from the body to the preheader.
To identify loop-invariant instructions:
(This determination requires that you already calculated reaching definitions! Presumably using data flow.)
It's safe to move a loop-invariant instruction to the preheader iff:
- The definition dominates all of its uses, and
- No other definitions of the same variable exist in the loop, and
- The instruction dominates all loop exits.
The last criterion is somewhat tricky: it ensures that the computation would have been computed eventually anyway, so it's safe to just do it earlier. But it's not true of loops that may execute zero times, which, when you think about it, rules out most for loops! It's possible to relax this condition if:
- The assigned-to variable is dead after the loop, and
- The instruction can't have side effects, including exceptions—generally ruling out division because it might divide by zero. (A thing that you generally need to be careful of in such speculative optimizations that do computations that might not actually be necessary.)
Static Single Assignment (SSA)
You have undoubtedly noticed by now that many of the annoying problems in implementing analyses & optimizations stem from variable name conflicts. Wouldn't it be nice if every assignment in a program used a unique variable name? Of course, people don't write programs that way, so we're out of luck. Right?
Wrong! Many compilers convert programs into static single assignment (SSA) form, which does exactly what it says: it ensures that, globally, every variable has exactly one static assignment location. (Of course, that statement might be executed multiple times, which is why it's not dynamic single assignment.) In Bril terms, we convert a program like this:
Into a program like this, by renaming all the variables:
Of course, things will get a little more complicated when there is control flow. And because real machines are not SSA, using separate variables (i.e., memory locations and registers) for everything is bound to be inefficient. The idea in SSA is to convert general programs into SSA form, do all our optimization there, and then convert back to a standard mutating form before we generate backend code.
Just renaming assignments willy-nilly will quickly run into problems. Consider this program:
If we start renaming all the occurrences of a , everything goes fine until we try to write that last print a . Which "version" of a should it use?
To match the expressiveness of unrestricted programs, SSA adds a new kind of instruction: a ϕ-node . ϕ-nodes are flow-sensitive copy instructions: they get a value from one of several variables, depending on which incoming CFG edge was most recently taken to get to them.
In Bril, a ϕ-node appears as a phi instruction:
The phi instruction chooses between any number of variables, and it picks between them based on labels. If the program most recently executed a basic block with the given label, then the phi instruction takes its value from the corresponding variable.
You can write the above program in SSA like this:
It can also be useful to see how ϕ-nodes crop up in loops.
(An aside: some recent SSA-form IRs, such as MLIR and Swift's IR , use an alternative to ϕ-nodes called basic block arguments . Instead of making ϕ-nodes look like weird instructions, these IRs bake the need for ϕ-like conditional copies into the structure of the CFG. Basic blocks have named parameters, and whenever you jump to a block, you must provide arguments for those parameters. With ϕ-nodes, a basic block enumerates all the possible sources for a given variable, one for each in-edge in the CFG; with basic block arguments, the sources are distributed to the "other end" of the CFG edge. Basic block arguments are a nice alternative for "SSA-native" IRs because they avoid messy problems that arise when needing to treat ϕ-nodes differently from every other kind of instruction.)
Bril in SSA
Bril has an SSA extension . It adds support for a phi instruction. Beyond that, SSA form is just a restriction on the normal expressiveness of Bril—if you solemnly promise never to assign statically to the same variable twice, you are writing "SSA Bril."
The reference interpreter has built-in support for phi , so you can execute your SSA-form Bril programs without fuss.
The SSA Philosophy
In addition to a language form, SSA is also a philosophy! It can fundamentally change the way you think about programs. In the SSA philosophy:
- definitions == variables
- instructions == values
- arguments == data flow graph edges
In LLVM, for example, instructions do not refer to argument variables by name—an argument is a pointer to defining instruction.
Converting to SSA
To convert to SSA, we want to insert ϕ-nodes whenever there are distinct paths containing distinct definitions of a variable. We don't need ϕ-nodes in places that are dominated by a definition of the variable. So what's a way to know when control reachable from a definition is not dominated by that definition? The dominance frontier!
We do it in two steps. First, insert ϕ-nodes:
Then, rename variables:
Converting from SSA
Eventually, we need to convert out of SSA form to generate efficient code for real machines that don't have phi -nodes and do have finite space for variable storage.
The basic algorithm is pretty straightforward. If you have a ϕ-node:
Then there must be assignments to x and y (recursively) preceding this statement in the CFG. The paths from x to the phi -containing block and from y to the same block must "converge" at that block. So insert code into the phi -containing block's immediate predecessors along each of those two paths: one that does v = id x and one that does v = id y . Then you can delete the phi instruction.
This basic approach can introduce some redundant copying. (Take a look at the code it generates after you implement it!) Non-SSA copy propagation optimization can work well as a post-processing step. For a more extensive take on how to translate out of SSA efficiently, see “Revisiting Out-of-SSA Translation for Correctness, Code Quality, and Efficiency” by Boissinot et al.
- Find dominators for a function.
- Construct the dominance tree.
- Compute the dominance frontier.
- One thing to watch out for: a tricky part of the translation from the pseudocode to the real world is dealing with variables that are undefined along some paths.
- You will want to make sure the output of your "to SSA" pass is actually in SSA form. There's a really simple is_ssa.py script that can check that for you.
- You'll also want to make sure that programs do the same thing when converted to SSA form and back again. Fortunately, brili supports the phi instruction, so you can interpret your SSA-form programs if you want to check the midpoint of that round trip.
- For bonus "points," implement global value numbering for SSA-form Bril code.
- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
Static Single Assignment (with relevant examples)
Static Single Assignment was presented in 1988 by Barry K. Rosen, Mark N, Wegman, and F. Kenneth Zadeck.
In compiler design, Static Single Assignment ( shortened SSA) is a means of structuring the IR (intermediate representation) such that every variable is allotted a value only once and every variable is defined before it’s use. The prime use of SSA is it simplifies and improves the results of compiler optimisation algorithms, simultaneously by simplifying the variable properties. Some Algorithms improved by application of SSA –
- Constant Propagation – Translation of calculations from runtime to compile time. E.g. – the instruction v = 2*7+13 is treated like v = 27
- Value Range Propagation – Finding the possible range of values a calculation could result in.
- Dead Code Elimination – Removing the code which is not accessible and will have no effect on results whatsoever.
- Strength Reduction – Replacing computationally expensive calculations by inexpensive ones.
- Register Allocation – Optimising the use of registers for calculations.
Any code can be converted to SSA form by simply replacing the target variable of each code segment with a new variable and substituting each use of a variable with the new edition of the variable reaching that point. Versions are created by splitting the original variables existing in IR and are represented by original name with a subscript such that every variable gets its own version.
Example #1:
Convert the following code segment to SSA form:
Here x,y,z,s,p,q are original variables and x 2 , s 2 , s 3 , s 4 are versions of x and s.
Example #2:
Here a,b,c,d,e,q,s are original variables and a 2 , q 2 , q 3 are versions of a and q.
Phi function and SSA codes
The three address codes may also contain goto statements, and thus a variable may assume value from two different paths.
Consider the following example:-
Example #3:
When we try to convert the above three address code to SSA form, the output looks like:-
Attempt #3:
We need to be able to decide what value shall y take, out of x 1 and x 2 . We thus introduce the notion of phi functions, which resolves the correct value of the variable from two different computation paths due to branching.
Hence, the correct SSA codes for the example will be:-
Solution #3:
Thus, whenever a three address code has a branch and control may flow along two different paths, we need to use phi functions for appropriate addresses.

Please Login to comment...
Similar reads, improve your coding skills with practice.
What kind of Experience do you want to share?
ENOSUCHBLOG
Programming, philosophy, pedaling., understanding static single assignment forms, oct 23, 2020 tags: llvm , programming .
This post is at least a year old.
With thanks to Niki Carroll , winny, and kurufu for their invaluable proofreading and advice.
By popular demand , I’m doing another LLVM post. This time, it’s single static assignment (or SSA) form, a common feature in the intermediate representations of optimizing compilers.
Like the last one , SSA is a topic in compiler and IR design that I mostly understand but could benefit from some self-guided education on. So here we are.
How to represent a program
At the highest level, a compiler’s job is singular: to turn some source language input into some machine language output . Internally, this breaks down into a sequence of clearly delineated 1 tasks:
- Lexing the source into a sequence of tokens
- Parsing the token stream into an abstract syntax tree , or AST 2
- Validating the AST (e.g., ensuring that all uses of identifiers are consistent with the source language’s scoping and definition rules) 3
- Translating the AST into machine code, with all of its complexities (instruction selection, register allocation, frame generation, &c)
In a single-pass compiler, (4) is monolithic: machine code is generated as the compiler walks the AST, with no revisiting of previously generated code. This is extremely fast (in terms of compiler performance) in exchange for some a few significant limitations:
Optimization potential: because machine code is generated in a single pass, it can’t be revisited for optimizations. Single-pass compilers tend to generate extremely slow and conservative machine code.
By way of example: the System V ABI (used by Linux and macOS) defines a special 128-byte region beyond the current stack pointer ( %rsp ) that can be used by leaf functions whose stack frames fit within it. This, in turn, saves a few stack management instructions in the function prologue and epilogue.
A single-pass compiler will struggle to take advantage of this ABI-supplied optimization: it needs to emit a stack slot for each automatic variable as they’re visited, and cannot revisit its function prologue for erasure if all variables fit within the red zone.
Language limitations: single-pass compilers struggle with common language design decisions, like allowing use of identifiers before their declaration or definition. For example, the following is valid C++:
| Rect { public: int area() { return width() * height(); } int width() { return 5; } int height() { return 5; } }; |
C and C++ generally require pre-declaration and/or definition for identifiers, but member function bodies may reference the entire class scope. This will frustrate a single-pass compiler, which expects Rect::width and Rect::height to already exist in some symbol lookup table for call generation.
Consequently, (virtually) all modern compilers are multi-pass .

Multi-pass compilers break the translation phase down even more:
- The AST is lowered into an intermediate representation , or IR
- Analyses (or passes) are performed on the IR, refining it according to some optimization profile (code size, performance, &c)
- The IR is either translated to machine code or lowered to another IR, for further target specialization or optimization 4
So, we want an IR that’s easy to correctly transform and that’s amenable to optimization. Let’s talk about why IRs that have the static single assignment property fill that niche.
At its core, the SSA form of any program source program introduces only one new constraint: all variables are assigned (i.e., stored to) exactly once .
By way of example: the following (not actually very helpful) function is not in a valid SSA form with respect to the flags variable:
| helpful_open(char *fname) { int flags = O_RDWR; if (!access(fname, F_OK)) { flags |= O_CREAT; } int fd = open(fname, flags, 0644); return fd; } |
Why? Because flags is stored to twice: once for initialization, and (potentially) again inside the conditional body.
As programmers, we could rewrite helpful_open to only ever store once to each automatic variable:
| helpful_open(char *fname) { if (!access(fname, F_OK)) { int flags = O_RDWR | O_CREAT; return open(fname, flags, 0644); } else { int flags = O_RDWR; return open(fname, flags, 0644); } } |
But this is clumsy and repetitive: we essentially need to duplicate every chain of uses that follow any variable that is stored to more than once. That’s not great for readability, maintainability, or code size.
So, we do what we always do: make the compiler do the hard work for us. Fortunately there exists a transformation from every valid program into an equivalent SSA form, conditioned on two simple rules.
Rule #1: Whenever we see a store to an already-stored variable, we replace it with a brand new “version” of that variable.
Using rule #1 and the example above, we can rewrite flags using _N suffixes to indicate versions:
| helpful_open(char *fname) { int flags_0 = O_RDWR; // Declared up here to avoid dealing with C scopes. int flags_1; if (!access(fname, F_OK)) { flags_1 = flags_0 | O_CREAT; } int fd = open(fname, flags_1, 0644); return fd; } |
But wait a second: we’ve made a mistake!
- open(..., flags_1, ...) is incorrect: it unconditionally assigns O_CREAT , which wasn’t in the original function semantics.
- open(..., flags_0, ...) is also incorrect: it never assigns O_CREAT , and thus is wrong for the same reason.
So, what do we do? We use rule 2!
Rule #2: Whenever we need to choose a variable based on control flow, we use the Phi function (φ) to introduce a new variable based on our choice.
Using our example once more:
| helpful_open(char *fname) { int flags_0 = O_RDWR; // Declared up here to avoid dealing with C scopes. int flags_1; if (!access(fname, F_OK)) { flags_1 = flags_0 | O_CREAT; } int flags_2 = φ(flags_0, flags_1); int fd = open(fname, flags_2, 0644); return fd; } |
Our quandary is resolved: open always takes flags_2 , where flags_2 is a fresh SSA variable produced applying φ to flags_0 and flags_1 .
Observe, too, that φ is a symbolic function: compilers that use SSA forms internally do not emit real φ functions in generated code 5 . φ exists solely to reconcile rule #1 with the existence of control flow.
As such, it’s a little bit silly to talk about SSA forms with C examples (since C and other high-level languages are what we’re translating from in the first place). Let’s dive into how LLVM’s IR actually represents them.
SSA in LLVM
First of all, let’s see what happens when we run our very first helpful_open through clang with no optimizations:
| dso_local i32 @helpful_open(i8* %fname) #0 { entry: %fname.addr = alloca i8*, align 8 %flags = alloca i32, align 4 %fd = alloca i32, align 4 store i8* %fname, i8** %fname.addr, align 8 store i32 2, i32* %flags, align 4 %0 = load i8*, i8** %fname.addr, align 8 %call = call i32 @access(i8* %0, i32 0) #4 %tobool = icmp ne i32 %call, 0 br i1 %tobool, label %if.end, label %if.then if.then: ; preds = %entry %1 = load i32, i32* %flags, align 4 %or = or i32 %1, 64 store i32 %or, i32* %flags, align 4 br label %if.end if.end: ; preds = %if.then, %entry %2 = load i8*, i8** %fname.addr, align 8 %3 = load i32, i32* %flags, align 4 %call1 = call i32 (i8*, i32, ...) @open(i8* %2, i32 %3, i32 420) store i32 %call1, i32* %fd, align 4 %4 = load i32, i32* %fd, align 4 ret i32 %4 } |
(View it on Godbolt .)
So, we call open with %3 , which comes from…a load from an i32* named %flags ? Where’s the φ?
This is something that consistently slips me up when reading LLVM’s IR: only values , not memory, are in SSA form. Because we’ve compiled with optimizations disabled, %flags is just a stack slot that we can store into as many times as we please, and that’s exactly what LLVM has elected to do above.
As such, LLVM’s SSA-based optimizations aren’t all that useful when passed IR that makes direct use of stack slots. We want to maximize our use of SSA variables, whenever possible, to make future optimization passes as effective as possible.
This is where mem2reg comes in:
This file (optimization pass) promotes memory references to be register references. It promotes alloca instructions which only have loads and stores as uses. An alloca is transformed by using dominator frontiers to place phi nodes, then traversing the function in depth-first order to rewrite loads and stores as appropriate. This is just the standard SSA construction algorithm to construct “pruned” SSA form.
(Parenthetical mine.)
mem2reg gets run at -O1 and higher, so let’s do exactly that:
| dso_local i32 @helpful_open(i8* nocapture readonly %fname) local_unnamed_addr #0 { entry: %call = call i32 @access(i8* %fname, i32 0) #4 %tobool.not = icmp eq i32 %call, 0 %spec.select = select i1 %tobool.not, i32 66, i32 2 %call1 = call i32 (i8*, i32, ...) @open(i8* %fname, i32 %spec.select, i32 420) #4, !dbg !22 ret i32 %call1, !dbg !23 } |
Foiled again! Our stack slots are gone thanks to mem2reg , but LLVM has actually optimized too far : it figured out that our flags value is wholly dependent on the return value of our access call and erased the conditional entirely.
Instead of a φ node, we got this select :
| = select i1 %tobool.not, i32 66, i32 2 |
which the LLVM Language Reference describes concisely:
The ‘select’ instruction is used to choose one value based on a condition, without IR-level branching.
So we need a better example. Let’s do something that LLVM can’t trivially optimize into a select (or sequence of select s), like adding an else if with a function that we’ve only provided the declaration for:
| filesize(char *); int helpful_open(char *fname) { int flags = O_RDWR; if (!access(fname, F_OK)) { flags |= O_CREAT; } else if (filesize(fname) > 0) { flags |= O_TRUNC; } int fd = open(fname, flags, 0644); return fd; } |
| dso_local i32 @helpful_open(i8* %fname) local_unnamed_addr #0 { entry: %call = call i32 @access(i8* %fname, i32 0) #5 %tobool.not = icmp eq i32 %call, 0 br i1 %tobool.not, label %if.end4, label %if.else if.else: ; preds = %entry %call1 = call i64 @filesize(i8* %fname) #5 %cmp.not = icmp eq i64 %call1, 0 %spec.select = select i1 %cmp.not, i32 2, i32 514 br label %if.end4 if.end4: ; preds = %if.else, %entry %flags.0 = phi i32 [ 66, %entry ], [ %spec.select, %if.else ] %call5 = call i32 (i8*, i32, ...) @open(i8* %fname, i32 %flags.0, i32 420) #5 ret i32 %call5 } |
That’s more like it! Here’s our magical φ:
| = phi i32 [ 66, %entry ], [ %spec.select, %if.else ] |
LLVM’s phi is slightly more complicated than the φ(flags_0, flags_1) that I made up before, but not by much: it takes a list of pairs (two, in this case), with each pair containing a possible value and that value’s originating basic block (which, by construction, is always a predecessor block in the context of the φ node).
The Language Reference backs us up:
The type of the incoming values is specified with the first type field. After this, the ‘phi’ instruction takes a list of pairs as arguments, with one pair for each predecessor basic block of the current block. Only values of first class type may be used as the value arguments to the PHI node. Only labels may be used as the label arguments. There must be no non-phi instructions between the start of a basic block and the PHI instructions: i.e. PHI instructions must be first in a basic block.
Observe, too, that LLVM is still being clever: one of our φ choices is a computed select ( %spec.select ), so LLVM still managed to partially erase the original control flow.
So that’s cool. But there’s a piece of control flow that we’ve conspicuously ignored.
What about loops?
| do_math(int count, int base) { for (int i = 0; i < count; i++) { base += base; } return base; } |
| dso_local i32 @do_math(i32 %count, i32 %base) local_unnamed_addr #0 { entry: %cmp5 = icmp sgt i32 %count, 0 br i1 %cmp5, label %for.body, label %for.cond.cleanup for.cond.cleanup: ; preds = %for.body, %entry %base.addr.0.lcssa = phi i32 [ %base, %entry ], [ %add, %for.body ] ret i32 %base.addr.0.lcssa for.body: ; preds = %entry, %for.body %i.07 = phi i32 [ %inc, %for.body ], [ 0, %entry ] %base.addr.06 = phi i32 [ %add, %for.body ], [ %base, %entry ] %add = shl nsw i32 %base.addr.06, 1 %inc = add nuw nsw i32 %i.07, 1 %exitcond.not = icmp eq i32 %inc, %count br i1 %exitcond.not, label %for.cond.cleanup, label %for.body, !llvm.loop !26 } |
Not one, not two, but three φs! In order of appearance:
Because we supply the loop bounds via count , LLVM has no way to ensure that we actually enter the loop body. Consequently, our very first φ selects between the initial %base and %add . LLVM’s phi syntax helpfully tells us that %base comes from the entry block and %add from the loop, just as we expect. I have no idea why LLVM selected such a hideous name for the resulting value ( %base.addr.0.lcssa ).
Our index variable is initialized once and then updated with each for iteration, so it also needs a φ. Our selections here are %inc (which each body computes from %i.07 ) and the 0 literal (i.e., our initialization value).
Finally, the heart of our loop body: we need to get base , where base is either the initial base value ( %base ) or the value computed as part of the prior loop ( %add ). One last φ gets us there.
The rest of the IR is bookkeeping: we need separate SSA variables to compute the addition ( %add ), increment ( %inc ), and exit check ( %exitcond.not ) with each loop iteration.
So now we know what an SSA form is , and how LLVM represents them 6 . Why should we care?
As I briefly alluded to early in the post, it comes down to optimization potential: the SSA forms of programs are particularly suited to a number of effective optimizations.
Let’s go through a select few of them.
Dead code elimination
One of the simplest things that an optimizing compiler can do is remove code that cannot possibly be executed . This makes the resulting binary smaller (and usually faster, since more of it can fit in the instruction cache).
“Dead” code falls into several categories 7 , but a common one is assignments that cannot affect program behavior, like redundant initialization:
| main(void) { int x = 100; if (rand() % 2) { x = 200; } else if (rand() % 2) { x = 300; } else { x = 400; } return x; } |
Without an SSA form, an optimizing compiler would need to check whether any use of x reaches its original definition ( x = 100 ). Tedious. In SSA form, the impossibility of that is obvious:
| main(void) { int x_0 = 100; // Just ignore the scoping. Computers aren't real life. if (rand() % 2) { int x_1 = 200; } else if (rand() % 2) { int x_2 = 300; } else { int x_3 = 400; } return φ(x_1, x_2, x_3); } |
And sure enough, LLVM eliminates the initial assignment of 100 entirely:
| dso_local i32 @main() local_unnamed_addr #0 { entry: %call = call i32 @rand() #3 %0 = and i32 %call, 1 %tobool.not = icmp eq i32 %0, 0 br i1 %tobool.not, label %if.else, label %if.end6 if.else: ; preds = %entry %call1 = call i32 @rand() #3 %1 = and i32 %call1, 1 %tobool3.not = icmp eq i32 %1, 0 %. = select i1 %tobool3.not, i32 400, i32 300 br label %if.end6 if.end6: ; preds = %if.else, %entry %x.0 = phi i32 [ 200, %entry ], [ %., %if.else ] ret i32 %x.0 } |
Constant propagation
Compilers can also optimize a program by substituting uses of a constant variable for the constant value itself. Let’s take a look at another blob of C:
| some_math(int x) { int y = 7; int z = 10; int a; if (rand() % 2) { a = y + z; } else if (rand() % 2) { a = y + z; } else { a = y - z; } return x + a; } |
As humans, we can see that y and z are trivially assigned and never modified 8 . For the compiler, however, this is a variant of the reaching definition problem from above: before it can replace y and z with 7 and 10 respectively, it needs to make sure that y and z are never assigned a different value.
Let’s do our SSA reduction:
| some_math(int x) { int y_0 = 7; int z_0 = 10; int a_0; if (rand() % 2) { int a_1 = y_0 + z_0; } else if (rand() % 2) { int a_2 = y_0 + z_0; } else { int a_3 = y_0 - z_0; } int a_4 = φ(a_1, a_2, a_3); return x + a_4; } |
This is virtually identical to our original form, but with one critical difference: the compiler can now see that every load of y and z is the original assignment. In other words, they’re all safe to replace!
| some_math(int x) { int y = 7; int z = 10; int a_0; if (rand() % 2) { int a_1 = 7 + 10; } else if (rand() % 2) { int a_2 = 7 + 10; } else { int a_3 = 7 - 10; } int a_4 = φ(a_1, a_2, a_3); return x + a_4; } |
So we’ve gotten rid of a few potential register operations, which is nice. But here’s the really critical part: we’ve set ourselves up for several other optimizations :
Now that we’ve propagated some of our constants, we can do some trivial constant folding : 7 + 10 becomes 17 , and so forth.
In SSA form, it’s trivial to observe that only x and a_{1..4} can affect the program’s behavior. So we can apply our dead code elimination from above and delete y and z entirely!
This is the real magic of an optimizing compiler: each individual optimization is simple and largely independent, but together they produce a virtuous cycle that can be repeated until gains diminish.
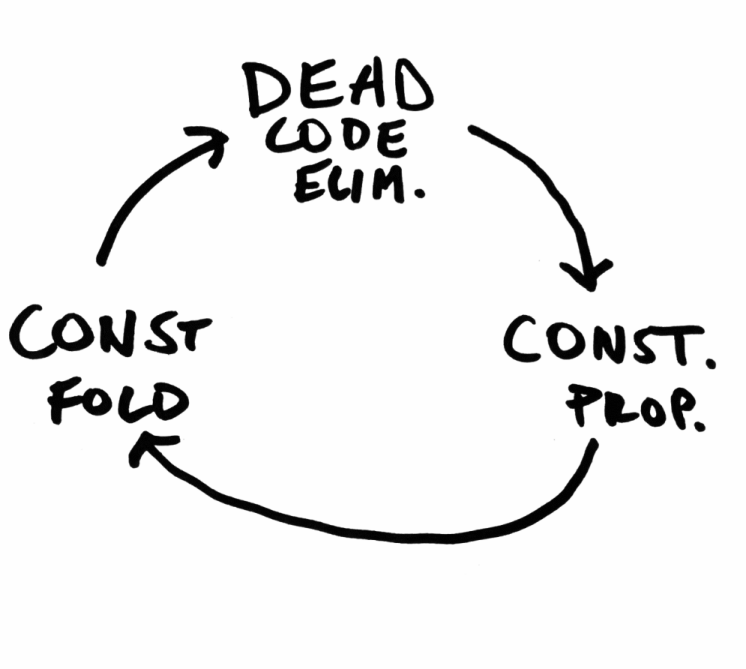
Register allocation
Register allocation (alternatively: register scheduling) is less of an optimization itself , and more of an unavoidable problem in compiler engineering: it’s fun to pretend to have access to an infinite number of addressable variables, but the compiler eventually insists that we boil our operations down to a small, fixed set of CPU registers .
The constraints and complexities of register allocation vary by architecture: x86 (prior to AMD64) is notoriously starved for registers 9 (only 8 full general purpose registers, of which 6 might be usable within a function’s scope 10 ), while RISC architectures typically employ larger numbers of registers to compensate for the lack of register-memory operations.
Just as above, reductions to SSA form have both indirect and direct advantages for the register allocator:
Indirectly: Eliminations of redundant loads and stores reduces the overall pressure on the register allocator, allowing it to avoid expensive spills (i.e., having to temporarily transfer a live register to main memory to accommodate another instruction).
Directly: Compilers have historically lowered φs into copies before register allocation, meaning that register allocators traditionally haven’t benefited from the SSA form itself 11 . There is, however, (semi-)recent research on direct application of SSA forms to both linear and coloring allocators 12 13 .
A concrete example: modern JavaScript engines use JITs to accelerate program evaluation. These JITs frequently use linear register allocators for their acceptable tradeoff between register selection speed (linear, as the name suggests) and acceptable register scheduling. Converting out of SSA form is a timely operation of its own, so linear allocation on the SSA representation itself is appealing in JITs and other contexts where compile time is part of execution time.
There are many things about SSA that I didn’t cover in this post: dominance frontiers , tradeoffs between “pruned” and less optimal SSA forms, and feedback mechanisms between the SSA form of a program and the compiler’s decision to cease optimizing, among others. Each of these could be its own blog post, and maybe will be in the future!
In the sense that each task is conceptually isolated and has well-defined inputs and outputs. Individual compilers have some flexibility with respect to whether they combine or further split the tasks. ↩
The distinction between an AST and an intermediate representation is hazy: Rust converts their AST to HIR early in the compilation process, and languages can be designed to have ASTs that are amendable to analyses that would otherwise be best on an IR. ↩
This can be broken up into lexical validation (e.g. use of an undeclared identifier) and semantic validation (e.g. incorrect initialization of a type). ↩
This is what LLVM does: LLVM IR is lowered to MIR (not to be confused with Rust’s MIR ), which is subsequently lowered to machine code. ↩
Not because they can’t: the SSA form of a program can be executed by evaluating φ with concrete control flow. ↩
We haven’t talked at all about minimal or pruned SSAs, and I don’t plan on doing so in this post. The TL;DR of them: naïve SSA form generation can lead to lots of unnecessary φ nodes, impeding analyses. LLVM (and GCC, and anything else that uses SSAs probably) will attempt to translate any initial SSA form into one with a minimally viable number of φs. For LLVM, this tied directly to the rest of mem2reg . ↩
Including removing code that has undefined behavior in it, since “doesn’t run at all” is a valid consequence of invoking UB. ↩
And are also function scoped, meaning that another translation unit can’t address them. ↩
x86 makes up for this by not being a load-store architecture : many instructions can pay the price of a memory round-trip in exchange for saving a register. ↩
Assuming that %esp and %ebp are being used by the compiler to manage the function’s frame. ↩
LLVM, for example, lowers all φs as one of its very first preparations for register allocation. See this 2009 LLVM Developers’ Meeting talk . ↩
Wimmer 2010a: “Linear Scan Register Allocation on SSA Form” ( PDF ) ↩
Hack 2005: “Towards Register Allocation for Programs in SSA-form” ( PDF ) ↩
Lab 7: Static Single-Assignment Form
In this lab, you will build a static single-assignment form (SSA) for your Tiger compiler to perform optimizations. SSA is a state-of-the-art IR also used in production compilers such as GCC or LLVM.
This lab consists of two parts: first, in part A, you will design and implement data structures defining the static single-assigment form. You will also implement translations from CFG to SSA as well as translations from SSA back to CFG. Second, in part B, you will implement several classic data-flow analysis and optimizations on SSA.
Getting Started
First check out the source we offered you for lab7:
these commands will first commit your changes to the lab6 branch of your local Git repository, and then create a local lab7 branch and check out the remote lab7 branch into the new local lab7 branch.
Do not forget to resolve any conflicts before commit to the local lab7 branch:
You should first import the new lab7 code into your favorite IDE, and make sure the code compiles. There are a bunch of new files that you should browse through:
Hand-in Procedure
When you finished your lab, zip you code and submit to the online teaching system .
Part A: Static Single-Assignment Form (SSA)
The static single-assignment form (SSA) is an important compiler intermediate representation, in which each variable is assigned (statically) at most once. SSA is more advantageous over other compiler IRs in that its single-assignment property makes program analysis and optimization simpler and more efficient. As a result, SSA has become a de-factor IR in modern optimizing compilers for imperative, OO, or even functional languages.
In this part of the lab, you will build a static single-assigment form for your Tiger compiler, and conduct optimizations based on your SSA IR. To aid in your implementation, we have given some hints for most exercises, but keep in mind that these hints are not mandatory, and you are free (and encouraged) to propose your own ideas.
SSA Data Structure
To better reuse your existing code base, you will implement SSA by leveraging data structures already designed for the control-flow graph. This design decision makes the interfaces cleaner and more elegant hence simplifying subsequent compilation phases.
Dominator Trees
You will be constructing the SSA form with the following 5 steps: 1) calculate dominators; 2) build dominator trees; 3) calculate dominance frontiers; 4) place φ-functions; and 5) rename variables.
In this part, you will finish the first two steps, that is, you will first calculate dominators then build a dominator tree for a given CFG.
Dominance Frontier
In this part of the lab, you will be implementing the third step to build an SSA, that is, you will calculate the dominance frontier for each node. The dominance frontier DF[n] of a node n is the set of all nodes d such that n dominates an immediate predecessor of d , but n does not strictly dominate d . Intuitively, the dominance frontier DF[n] for a node n is the set of nodes where n 's dominance stops.
φ-function Placement
In this part, you will implement the fourth step to build an SSA, that is, you will be implementing the φ-function placement. The φ-function placement algorithm places φ-functions at the top of corresponding blocks. Specifically, for a definition
to a variable x in a basic block n , this algorithm will place a φ-function
at the top of each n 's dominance frontier d ∈ DF[n] .
Renaming the Variables
In this part of the lab, you will be implementing the fifth and last step to build an SSA, that is, you will rename variables to make its definition unique.
To this point, your Tiger compiler can convert all legal MiniJava programs to SSA forms. Do regression test your Tiger compiler and fix potential bugs.
Translation Out of SSA Forms
Modern machines do not support the φ-functions directly, hence φ-functions must be eliminated before execution. This task is accomplished by the translation out of SSA forms.
To this point, your Tiger compiler can convert any SSA form back to a corresponding CFG. Do not forget to regression test your Tiger compiler.
Part B: SSA-based Optimizations
SSA makes compiler optimizations not only easier to engineer but also more efficient to execute, largely due to its single-assignment property. This nice property make it much easier to calculate the data-flow information required to perform optimizations.
In this part of the lab, you will re-implement several optimizations that we have done on the CFG on SSA again: dead code-elimination, constant propagation, copy propagation, among others. And you will also implement several novel optimizations that are particularly suitable for SSA: conditional constant propagation, global value numbering, among others.
Dead-code Elimination
In SSA, a statement x = e is dead, if the variable x is not used by any other statement (and e does not have side effects). As a result, this statement x = e can be safely eliminated.
Constant Propagation
In SSA, given a statement of the form x = c in which c is a constant, we can propagate the constant c to any use of variable x .
Copy Propagation
In SSA, given a copy statement x = y , then any use of x can be replaced by y .
φ-function Elimination
In SSA, if a φ-function is of a special form taking a list of same arguments:
where c is a constant, then this φ-function can be eliminated by rewriting it to a normal assignment to x :
Note that, often the time, this special form of φ-function x = φ(c, c, ..., c) might be generated by constant propagation optimizations, which substituted φ-function arguments by constants.
Similarly, the φ-function:
can be eliminated by rewriting it to an assignment statement:
where y is a variable.
Conditional Constant Propagation
Global value numbering, partial redundancy elimination.
Do not forget to test Tiger compiler after finishing all these optimizations.
Part C: SSA Program Analysis
This completes the lab. Remember to hand in your solution to the online teaching system.

IMAGES
VIDEO
COMMENTS
The choice between static and mobile patrols is guided by the property's expanse and structure. While static guards offer concentrated vigilance, mobile patrols echo expansive surveillance. Budget is a determining factor. Static guards offer intensive security but at a higher cost. Mobile patrols, with their expansive coverage, present a cost ...
Posted by u/[Deleted Account] - 7 votes and 18 comments
Recommendations for static guarding are given in BS 7499. This British Standard assists procurers of mobile patrol services such as security companies and ... routine communication to verify the location and status of a mobile patrol officer on an assignment 3.3 competent person person, suitably trained and qualified by knowledge and practical ...
Static security personnel are best suited in locations where constant surveillance of people or assets operating in a fixed area are required. Whether this is high-value stock in a retail space or secure areas in a building, static securitiy personnel are able to provide the unbroken surveillance you need to minimise the chance of a breach. ...
According to the static and dynamic environments of the execution process, the patrol task collaboration distribution can be divided into centralized and distributed collaboration. ... It indicates that two USVs are used for patrol task assignment, with each USV have a preset departure number 2, i.e., every time the total number of elements ...
Vigilant monitoring of entrances and exits: Security guards should pay close attention to all entrances and exits, ensuring they are secure and free from any unauthorized access. This includes checking for broken locks, propped-open doors, or any signs of tampering. Identifying out-of-place objects or signs: Security guards should be observant ...
A task assignment is a combinatorial and open-loop optimization process that minimizes a predefined objective function by assigning single or multiple agents to multiple tasks. Task assignment is efficient if all the tasks are completed appropriately, satisfying the constraints, and is fundamental in many multi-agent-based applications.
an assignment 3.3 competent person person, suitably trained and qualified by knowledge and practical experience, ... person who performs duties at a static site or on a mobile patrol 3.14 static site fixed location or premises to which a security officer is assigned for a fixed length of time 3.15 supplier individual or company (and the persons ...
For example, if you use the following commands to create two static routes for network 30.0.0/8, the route will place the first route to the routing table. #ip route 30.0.0.0 255.0.0.0 20.0.0.2 10 #ip route 30.0.0.0 255.0.0.0 40.0.0.2 20. If the first route fails, the router automatically adds the second route to the routing table.
Mobile Security Patrol. Mobile security patrols are simply security guards that move around your premises to ensure order. This might be particularly relevant out of hours, when crime might be more likely. While a CCTV system with the latest sensors and alarms is helpful to monitor a wide area, there will be places that the cameras can't reach.
Intuitively: The dominance frontier indicates a join point of control flow where two or more potential definitions can come together. DF(v) dominance frontier of v is a set. DF(v) includes w iff. v dominates some predecessor of w. v does not strictly dominate w DF(v) = {w|(∃u ∈ PRED(w)) [v DOM u] ∧ v DOM! w}
Static single assignment, known as SSA, was once developed at IBM Research.Because of its fast and powerful abilities on optimizations, most of the current commercial and open-source compilers, including LLVM, GCC, HotSpot, V8 engine, use SSA as a key IR for program analysis and other usages. On the other hand, research about Intermediate Representation such as MLIR became more mature.
Many compilers convert programs into static single assignment (SSA) form, which does exactly what it says: it ensures that, globally, every variable has exactly one static assignment location. (Of course, that statement might be executed multiple times, which is why it's not dynamic single assignment.) In Bril terms, we convert a program like this:
SSA. Static single assignment is an IR where every variable is assigned a value at most once in the program text. E as y for a b asi c bl ock : assign to a fresh variable at each stmt. each use uses the most recently defined var. (Si mil ar to V al ue N umb eri ng) Straight-line SSA. . + y.
In Static Single Assignment (SSA) Form each assignment to a variable, v, is changed into a unique assignment to new variable, v i. If variable v has n assignments to it throughout the program, then (at least) n new variables, v 1 to v n, are created to replace v. All uses of v are replaced by a use of some v i.
An ALNS-based approach for the traffic-police-routine-patrol-vehicle assignment problem in resource allocation analysis of traffic crashes. Jibiao Zhou a School of Civil and Transportation Engineering, ... Two resolution methods, the global static resolution mode, and real-time dynamic resolution mode, were applied to explore the optimal ...
Static Single Assignment was presented in 1988 by Barry K. Rosen, Mark N, Wegman, and F. Kenneth Zadeck.. In compiler design, Static Single Assignment ( shortened SSA) is a means of structuring the IR (intermediate representation) such that every variable is allotted a value only once and every variable is defined before it's use. The prime use of SSA is it simplifies and improves the ...
With thanks to Niki Carroll, winny, and kurufu for their invaluable proofreading and advice.. Preword. By popular demand, I'm doing another LLVM post.This time, it's single static assignment (or SSA) form, a common feature in the intermediate representations of optimizing compilers.. Like the last one, SSA is a topic in compiler and IR design that I mostly understand but could benefit from ...
Static Single Assignment. Idea: each assignment of variables to be given a unique name; each use of a variable to be reached by only one definition of that variable. Need to create F functions at join nodes reached by more than one definition of same variable. Dominance frontier is a subset of these join nodes where.
In this lab, you will build a static single-assignment form (SSA) for your Tiger compiler to perform optimizations. SSA is a state-of-the-art IR also used in production compilers such as GCC or LLVM. This lab consists of two parts: first, in part A, you will design and implement data structures defining the static single-assigment form.
Connects definitions of variables with uses of them. Propagate dataflow facts directly from defs to uses, rather than through control flow graph. In SSA form, def-use chains are linear in size of original program; in non-SSA form may be quadratic. Is relationship between SSA form and dominator structure of CFG.
President Biden did not assign her the job title of "border czar" or the responsibility of overseeing the enforcement policies at the U.S.-Mexico border, as the Trump campaign suggested on ...